Abusing network shares for efficient lateral movements and privesc (DirSharePivot)
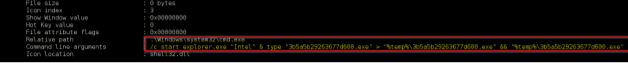
Background About a year ago my team and I had were called to perform a forensic analysis on a customer network. The reason for this was that a computer was first infected by a ransomware, and for some (unknown) reasons, several other workstations were getting "infected" after only 3 hours. After 5 hours (time of my intervention) I discovered that: - 80% of the workstations were infected - The network was partially segmented but the infection occurs on all segments - A malware process was even running on the file Server as... "Domain Administrator" :-/ - No track of 4624 (Logon Type 3) events or any other track of lateral movements/authentications Interesting... hum :) In this article I will describe my analysis of the threat and also how to take advantage of this method in a "safer" and more "controlled" way to move laterally (or even perform privesc) in red team operations. (practical exploitation code will be provided).